Full Guide: What Is Image EXIF Metadata, and How Do You Remove It?
Hidden in every image on your phone or computer is a set of metadata labeled EXIF data that stores additional information about that image.
EXIF stands for Exchangeable Image File Format. It's a standard that defines how to store ancillary information about an image, such as the GPS coordinates of where it was taken, the type of compression used, and even the camera's settings when the shot was taken.
Metadata refers to additional data about an item itself. It derives from the Greek word meta, which means "after" or "across." In computer science, metadata typically refers to data about an entity that isn't necessary for the entity to exist on its own. In other words, the image data is the pixels, colors, and details. Metadata is additional information about those pixels.
Removing image data, such as the color in a pixel, or the pixel itself, would ruin the image. But removing metadata won't.
What EXIF Data Can Be Stored
The EXIF standard contains over 400 tags! Each tag is associated with a number stored alongside the image.
Images can also store other metadata, not technically EXIF tags, but which form part of other metadata standards developed later.
ExifViewer.com lets you view metadata from all standards.
The EXIF tags can be generally grouped under the following:
- Camera settings: This is information like aperture, camera model, shutter speed, focal length, and other photo-specific information that makes it easier to analyze or categorize the photo later.
- Image metrics: Pixel dimensions, resolutions, etc.
- Date and time: This is the date and time according to the device you took the photo on. If the device time is wrong or set to a different timezone, then the image time will be wrong.
- Location data: Latitude and longitude info, which is a key privacy concern regarding EXIF data that we discuss below.
- Thumbnail version: This is so you can see a low-resolution version of the photo in galleries or on the screen of your digital camera without having to load the entire photo (which might be many megabytes large) into memory.
- Descriptions: Various tags that describe the image, the software used to create it, or even to associate a unique identifier for the image. One of the description tags is the UserComment tag where users can insert more detailed information about the image. When editing images on software that allows you to add descriptions, sometimes those descriptions are added to the UserComment tag. This tag can contain sensitive information that should be removed when uploading the image to a website.
- Copyright information: Two copyright tags exist, one for the image copyright and the other for the color profile. A color profile is software code that ensures colors are reproduced exactly as intended. Color profiles are copyrighted by their manufacturers. The EXIF standard also has an image copyright tag which allows the photographer and the editor to insert their respective copyrights into the image.
EXIF Isn't the Only Metadata Standard
Other metadata standards exist that allow additional info to be stored with an image.
XMP (Extensible Metadata Platform)
This standard was developed by Adobe. Unlike the EXIF standard, it omits camera- and image-related info.
The standard was originally proprietary but has since become an ISO (International Standards Organization) standard. Adobe originally released XMP in 2001 as part of Adobe Acrobat 5.0 (XMP metadata can also be embedded in PDFs).
IPTC (International Press Telecommunications Council) Metadata
This standard predates the EXIF standard and is, according to the official website, "the most widely used standard to describe photos." The standard is universally accepted among news agencies, museums, photographers, and photo agencies.
The modern standard consists of two "schemas" (descriptions of data): The Core schema and the Extension schema.
The standard contains extensive fields to describe specific people, locations, and even products in an image, making images with this kind of data in them a privacy nightmare.
For example, on the IPTC website, it's possible to download images that contain demo data in the form of IPTC tags. As you can see below, the IPTC tags are extensive and can contain private data such as the creator's name and zip code. The modern version of IPTC tags even contains tags for the AI tool used to generate an image.
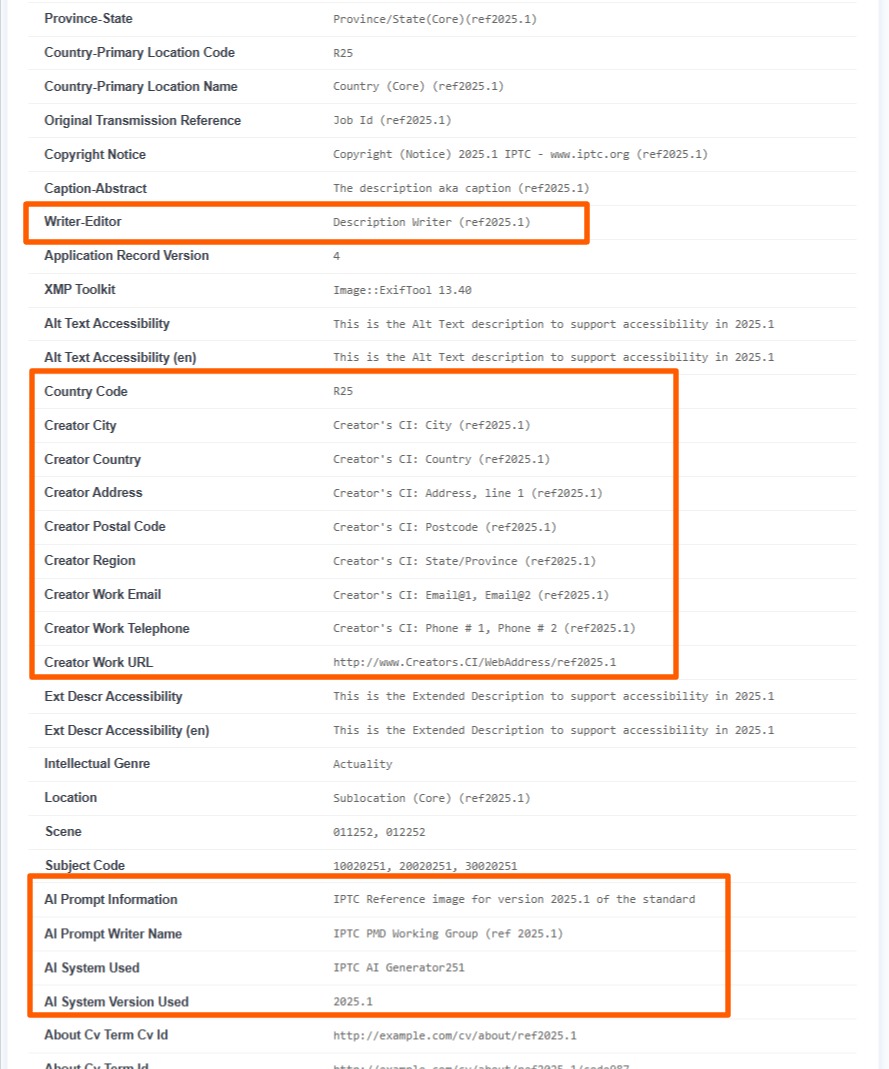
IPTC metadata serves a different purpose than EXIF data because it was created by a journalistic organization whose purpose was to describe images easily without having to attach long text descriptions and documents to the image.
IPTC standards also contain extensive copyright information tags, which are necessary to properly credit photographers for an image.
Stock photography websites use IPTC tags to embed licensing and copyright information in images. For example, when we view an image from a stock photography site on the official IPTC metadata viewer page, we can see various copyright- and license-related tags defined, as you can see below.
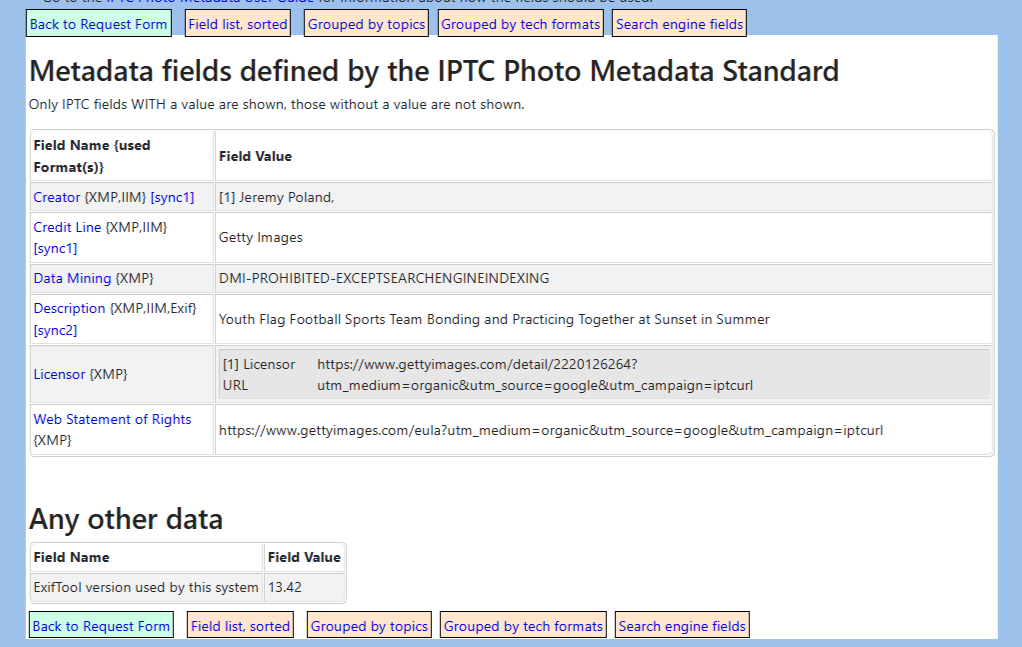
The reason you see "XMP" instead of IPTC is because IPTC uses the XMP format to store its tags.
The Risk of EXIF Data
Any textual data can be stored as metadata in an image. The device that takes or edits the image is the one that stores the data. It's also possible to store a person's name as part of metadata, as you saw in the examples above.
It's technically also possible to host malicious code scripts in EXIF data, giving hackers the ability to run code on a web server that reads that image.
The most common security risk, however, is when photos contain GPS coordinates, which many phones store automatically when you take a photo. Hackers and cybercriminals can use these GPS coordinates to either directly find where you are, or combine them with other online data to indirectly determine the same.
For example, a criminal might see a photo you posted of your new fancy car, read the EXIF data, and know where you are.
Ideally, the websites you upload photos to should strip away EXIF data, but there's no guarantee that they do. You're far safer stripping the data off yourself through a tool such as ExifViewer.com.
EXIF Data and AI-Generated Images
In an AI world, it's becoming increasingly difficult to determine if images are legitimate or not.
The Coalition for Content Provenance and Authenticity, or C2PA, has created open standards to help people determine the origin of photos. The standards are called "Content Credentials" and they're basically a set of EXIF tags that software can embed into images to determine where an image came from and what edits were done on them.
It's up to software vendors to implement C2PA.
Using ExifViewer.com, you can look at an image's EXIF data to see if any of the C2PA tags exist.
For example, we generated an image using Google Gemini and then uploaded it to ExifViewer.com to view its EXIF data. The image has the relevant Content Credentials that tell the user where the image came from.
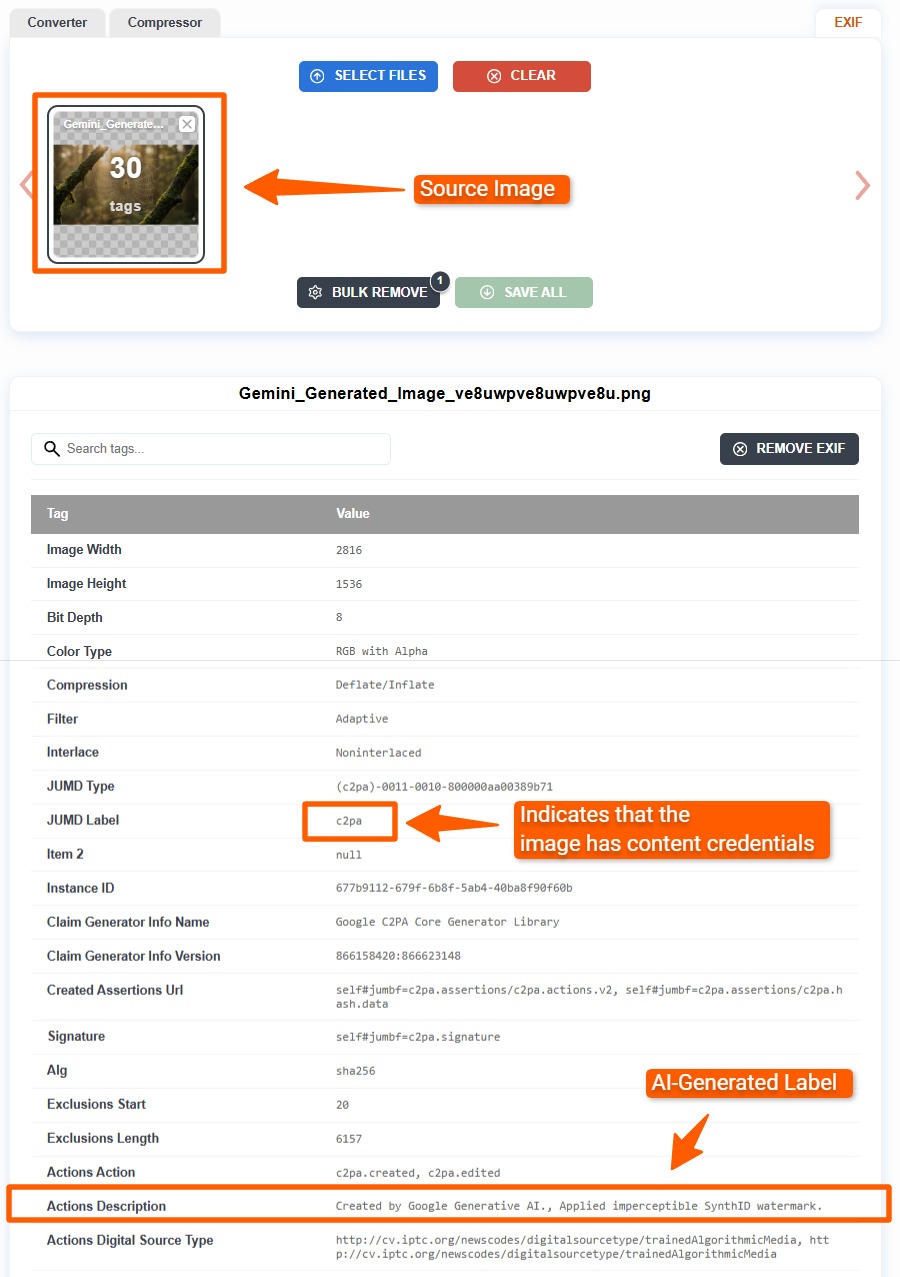
The image also contains a signature that validates the credentials. If anyone tampers with the image or the EXIF data, they invalidate the signature.
Note, however, that not all AI image generators honor the Content Credentials standard. For example, the image below, generated by the Grok AI tool, lacks any form of Content Credentials.
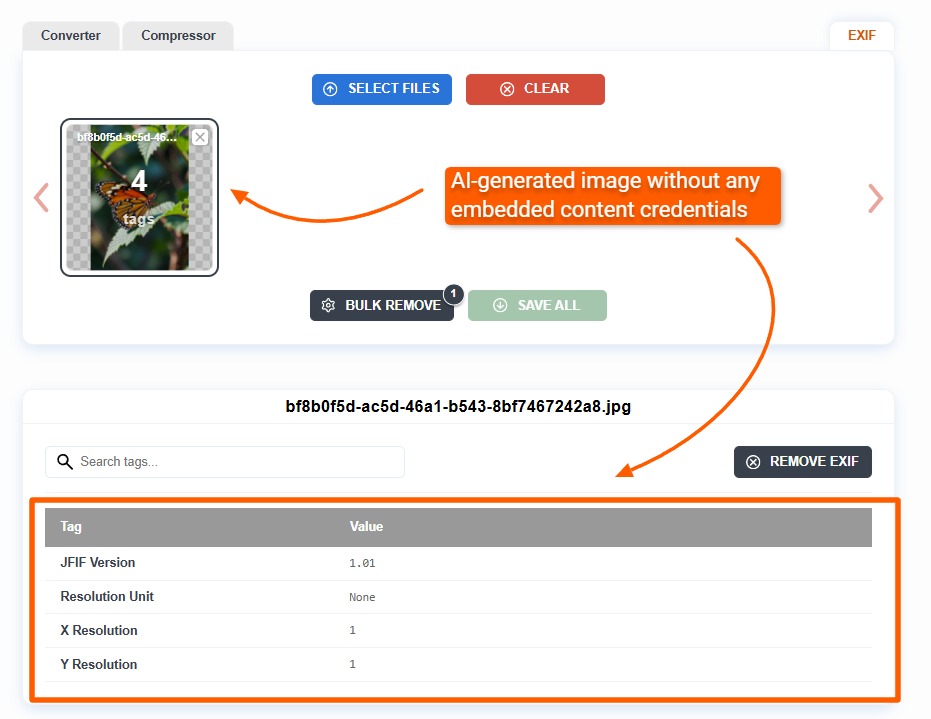
More and more technology companies, such as Google, Canon, Sony, and others, are starting to support C2PA metadata in their images. Their latest devices embed signed C2PA metadata, allowing users to verify the originality of an image and whether it has been edited or not.
Moving forward, it's highly probable that the lack of Content Credentials will become the red flag when looking at an image's EXIF data. In other words, right now, "the picture is the proof." But AI has turned that on its head. Moving forward, the validated Content Credentials stored in EXIF metadata will be the proof, right down to what edits were made.
Meanwhile, you can use ExifViewer.com to validate any suspicious images you find on the internet to see if they were generated by AI.
Secure Uploads Using ExifViewer.com
Before we get into the good stuff (namely, how to view and remove EXIF data using ExifViewer.com), it's important to say something about ExifViewer's security.
When you use ExifViewer.com, your uploaded image never leaves your device. All processing happens 100% on your computer, tablet, phone, or whatever other device you're using.
This approach is the opposite of how most other EXIF viewers work, and yet it's crucial.
When you're uploading images with potentially sensitive EXIF data in them, you don't want that data stored anywhere except on your personal device!
Most other EXIF viewing and removal tools will upload your photo to their servers before processing it. You have absolutely zero control over what happens with those photos when you upload them. You don't know how long they'll be stored, where they're stored, or even if that website is reputable and trustworthy.
Imagine wanting to remove sensitive EXIF data from a batch of photos (such as GPS coordinates), but you must first send the full GPS data to an external server before you're allowed to do it...
It makes no sense.
That's why ExifViewer.com works 100% inside your browser.
How to View EXIF Metadata with ExifViewer.com
ExifViewer.com provides two core functions:
- Viewing EXIF data
- Removing EXIF data
To view EXIF data for one or more photos, either click the "Select Files" button or drag files from your computer into the drag area.
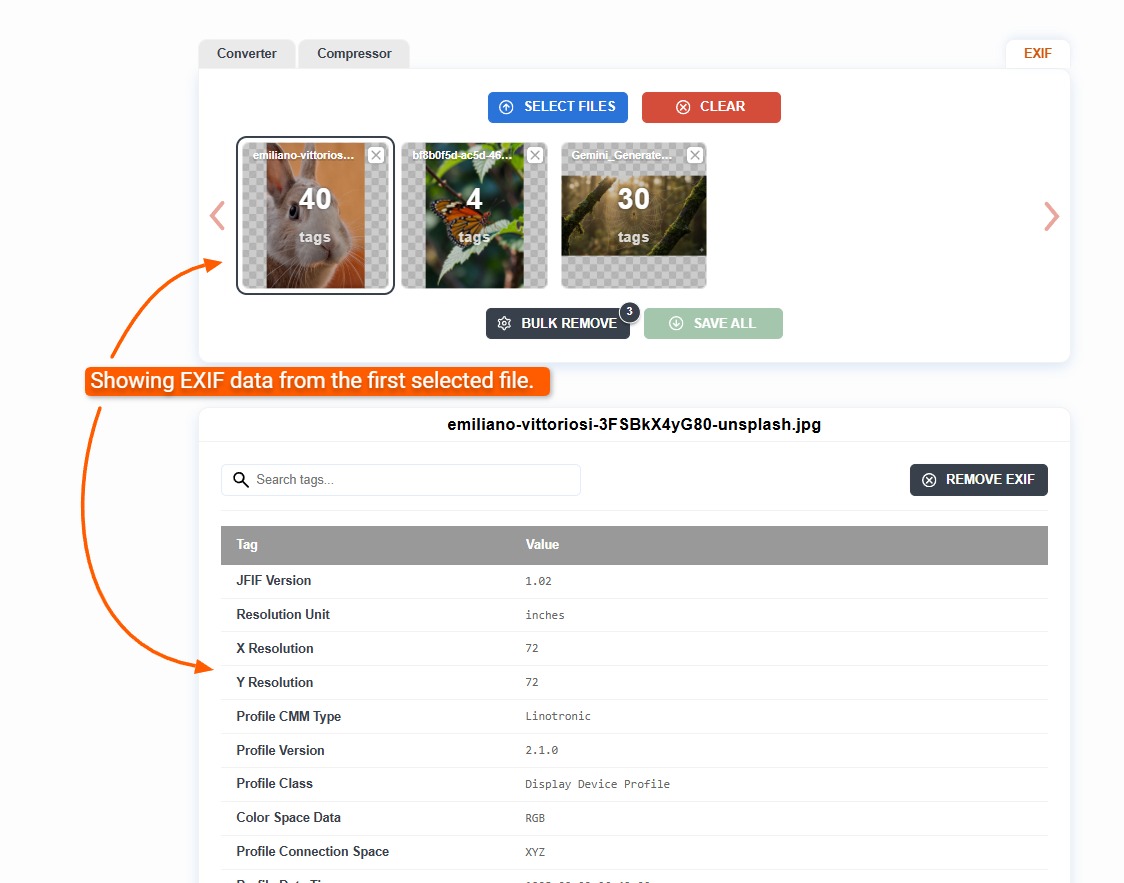
You can view EXIF data for multiple files at once. After uploading your files, just select the file for which you want to view EXIF data, and the data appears below it.
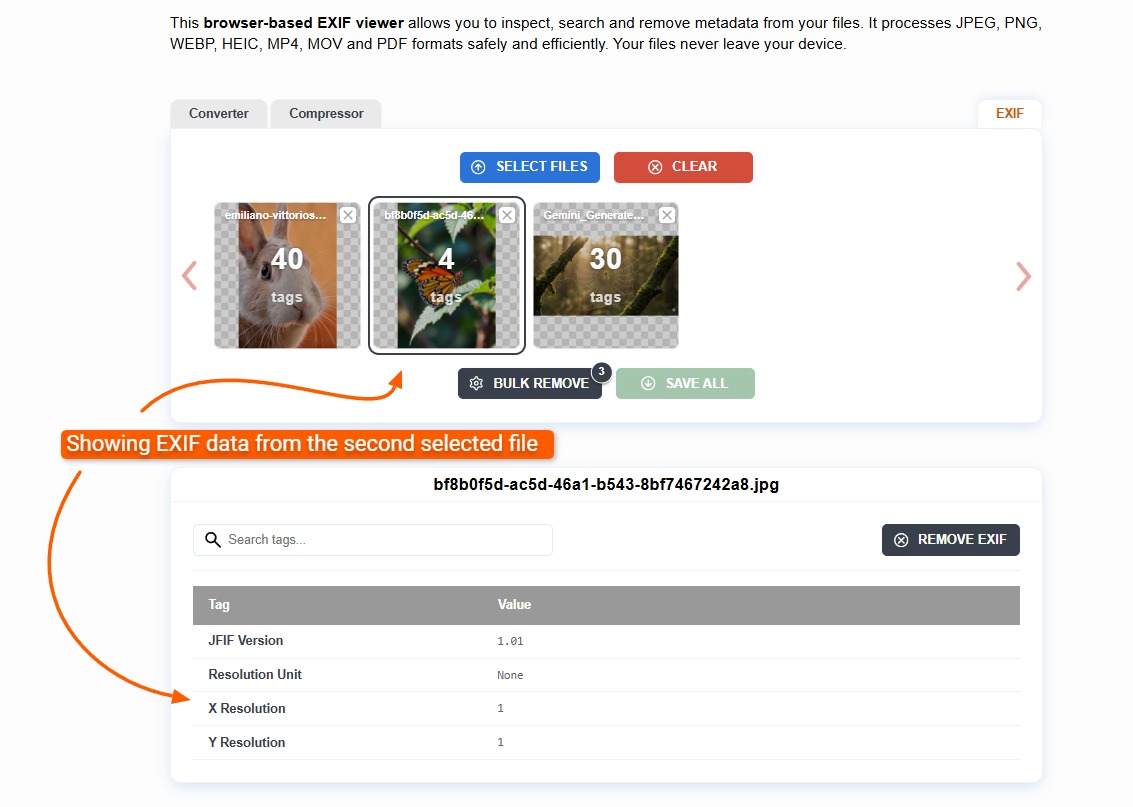
Some EXIF data can be confusing and related to technical standards. For example, the JFIF tag stands for "JPEG File Interchange Format." It's essentially a container format that contains a JPEG inside it and makes it easier for software to recognize and decode the file.
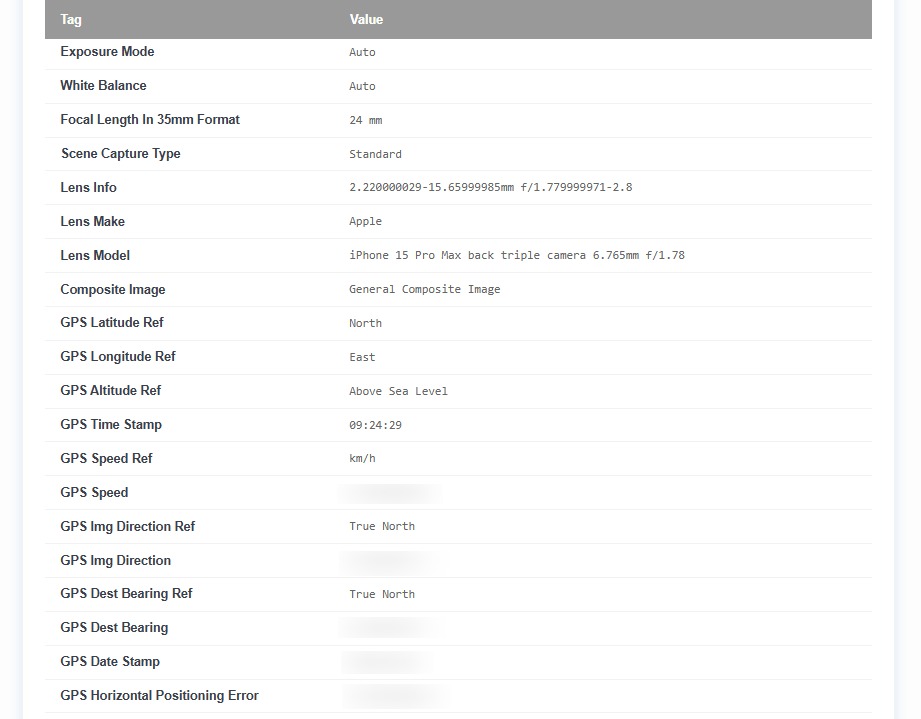
However, most of the "risky" EXIF data is easy to spot. For example, in the image below, taken with an iPhone, you can see all the GPS data, including the precise location where the photo was taken.
Even though most of the settings are highly technical, it's easy to tell one thing: you probably don't want such information shared with external websites.
How to Remove EXIF Metadata with ExifViewer.com
After uploading one or more images to ExifViewer.com, you can either remove the EXIF data in bulk or one by one. If you want to remove it one by one, just make sure you've selected the correct image before clicking the "Remove EXIF" button.
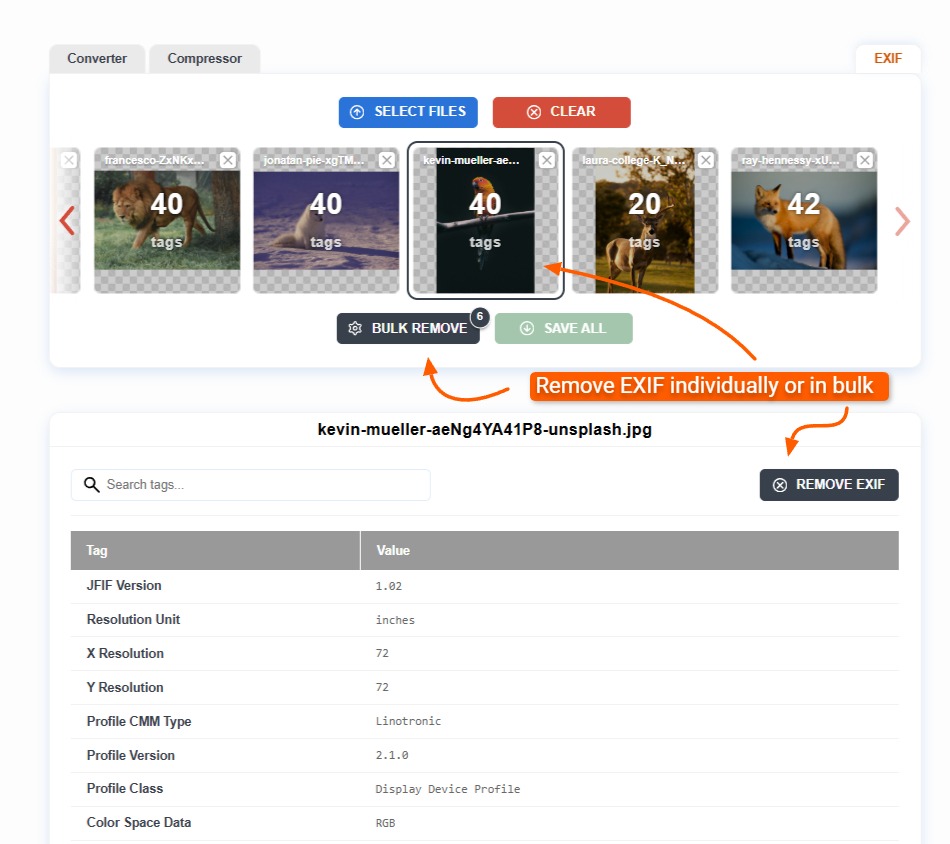
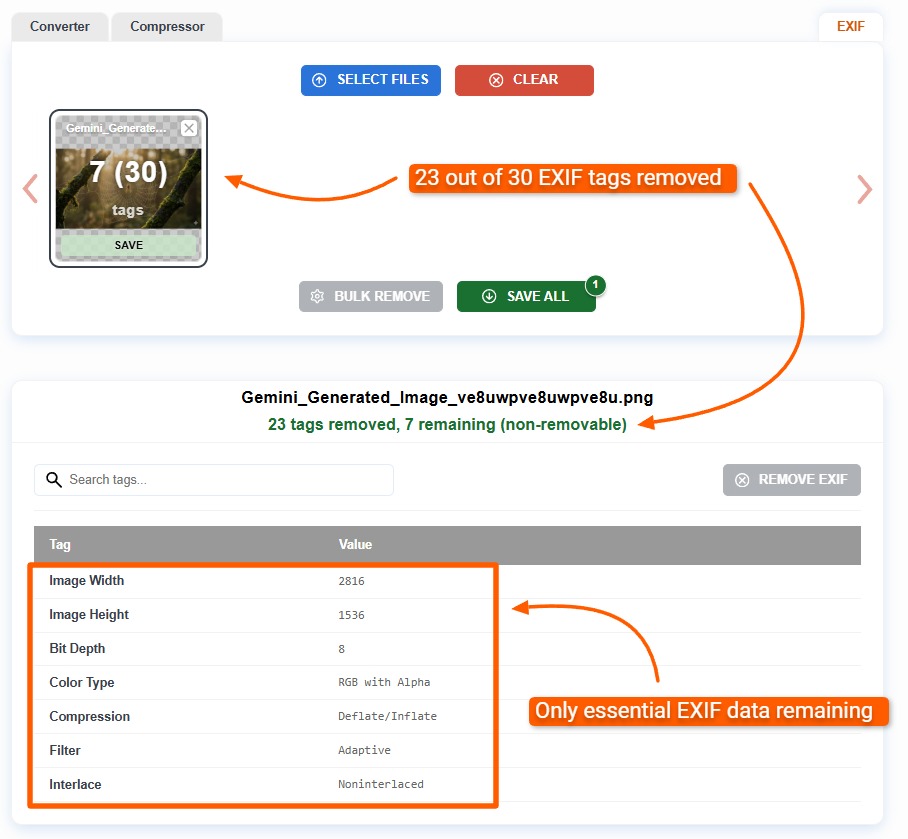
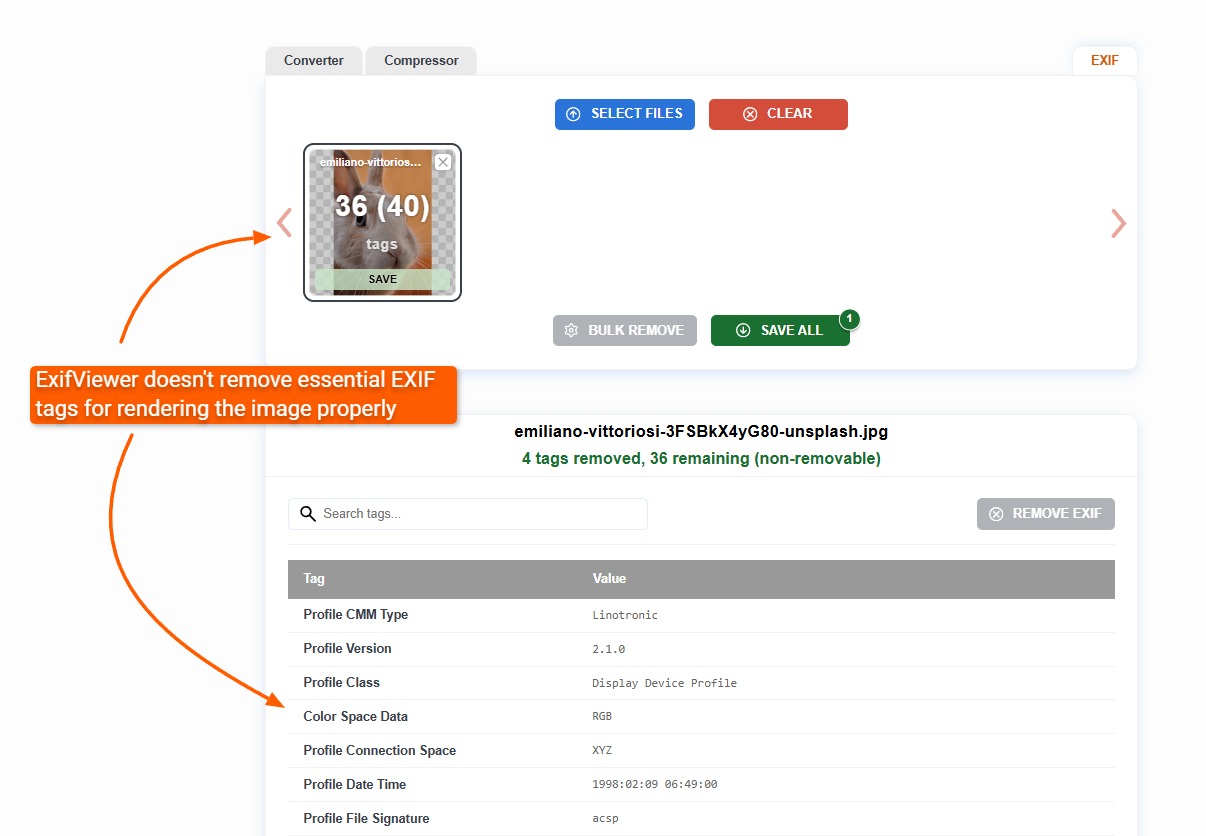
Unlike other tools that will damage your image, ExifViewer.com maintains any EXIF tags that are essential for rendering the image.
As you can see below, tags related to the image's color space and other essential rendering data are maintained. If we removed these tags, the image would change visually, which isn't the point of removing EXIF tags.

In this user's case, they were able to solve the problem by specifying more parameters to their EXIF removal tool to keep the essential EXIF data. That's quite complicated. The beauty of ExifViewer.com is that you don't have to install software or type in parameters. You just upload your image, and it works.
You can even operate it from your phone because it all runs in the browser.
Summary
EXIF data can pose security and privacy risks, but removing all EXIF data can also damage images.
Removing EXIF data is possible with special software that can be installed on a computer, but most people don't have the time or inclination to do that.
Some of that software also comes at a price.
Online tools are the other option. However, many of them either remove too much EXIF data, potentially damaging the image, while others require you to send the image to their servers, which poses a security risk.
The best solution is to use a tool that keeps your files 100% on your machine, runs on any device, and is totally free. That service is ExifViewer.com.
